Mueller Report
These are just my notes about the operational security pieces that are relevant to the US’s Mueller report about Russian interference with US elections of 2016. You can read the full report as well of course.
Attack A
Intrusions/initial attack vectors
Spearphishing (p38)
The DNC/DCCC attacker using Spearphishing in order to get administrator level access to some machines that were behind a VPN on their network.

Lateral movement: Email server, share file server, misc machines (p38) Within a month, the attackers spread inside the network. How they did this is unspecified. It appears Podesta was amongst the Spearphished (success or failure unspecified)
Persistence
Tooling
- RAR (Remote control, Windows - 332A1AEE7126C425EFDFD5B33FA922AA)
- mimikatz (Automated credential extractor)
- X-Agent S0314 S0023 CHOPSTICK (Remote control, multiplatform)
- X-Tunnel (proxy tool)
Methods
https://amscontrolpanel.com/ was utilized as an all-purpose jump-host for all operations, with the benefit to be US-hosted and to provide an additional layer of proxying.
Data exfiltration
Type/amount of data exfiltrated.
- Passwords
- Internal communication between humans
- Banking information
- PII
- Emails (the ones released by Wikileaks in 2016, ~33K)
- Docs (~50K Podesta)
- ~2.5GB total from “internal” network (p43)
- ~300GB from cloud snapshots (p50)
Domain registration (p42)
Domains were registered for the purposes of the hack and paid for with Bitcoins to avoid traceability, such as dcleaks.com
Accounts used
- Twitter @dcleaks_
- dcleaksproject@gmailc.om
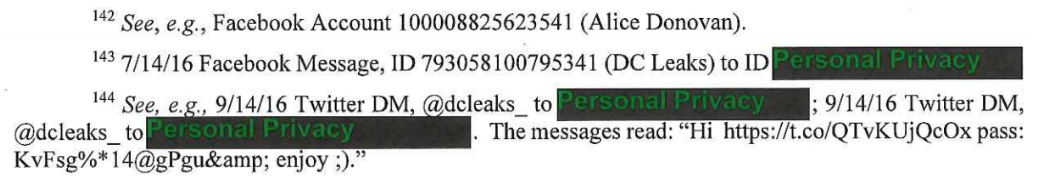
Password data was apparently transferred in clear text to these accounts by the hackers, using their messaging capabilities.
Attack concealment and “misleads”
(p42)
Within 1 hour of the announce of the hack, attackers ran several search with specific keywords. The attackers then attributed the attack to someone else and fabricated a story, where that attacker would have used these specific keywords.
Incident response & forensics work
Privileged access that helped:
- Twitter, Facebook, Gmail accounts and messages were under the FBI/CIA/NSA? Supervision and they have full access
What did not work:
- GPG encrypted files were apparently not decrypted
Attack B
Intrusions/initial attack vectors
SQL Injection (p50)

Spearphishing
With a word doc including a trojan.

Misc interesting data
Site passwords

Previous compromises
Hillary’s email server(p62)


Comments